Defense in Depth for Cloud Native Infrastructure
Published:
In modern Distributed Systems, security cannot be an afterthought bolted onto production. It must be designed in—from the moment a product idea is sketched to its continuous runtime operation.
The secure SDLC extends beyond development; it spans product planning, architecture, development, launch readiness, general availability, and ongoing operations. At each stage, security is embedded to ensure we detect and mitigate threats early, prevent vulnerabilities, and maintain compliance without slowing delivery.
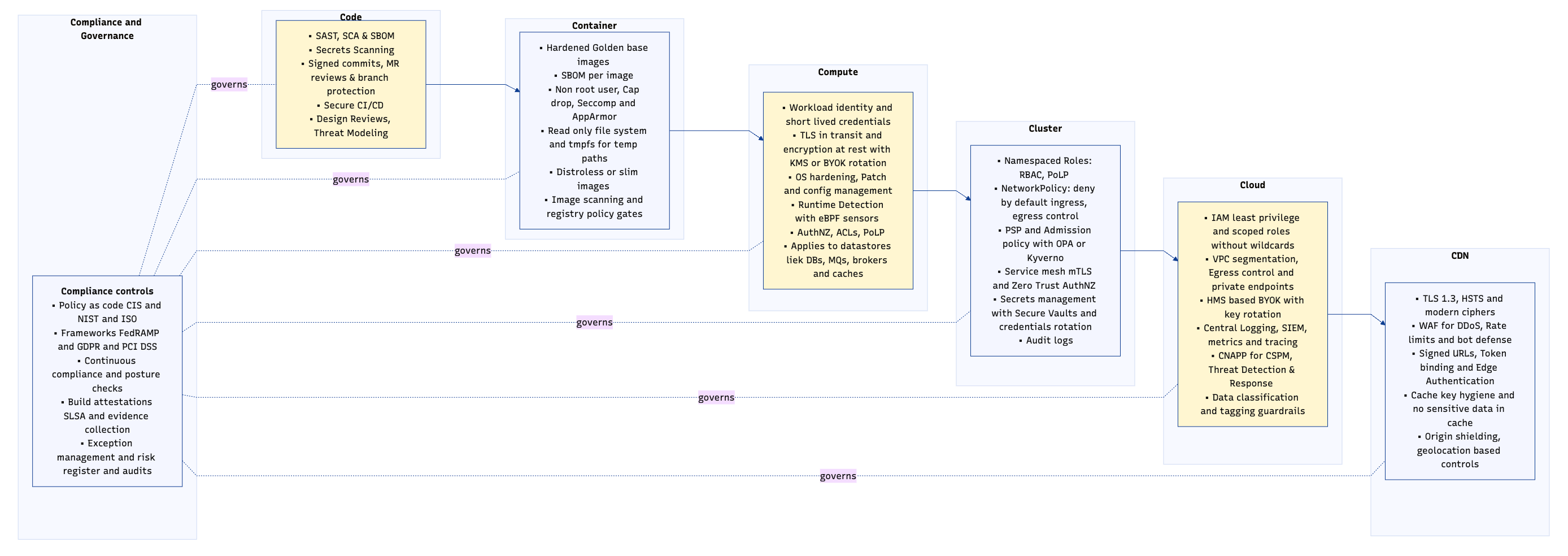
Designing a Secure SDLC for Multi-Cloud, Distributed Platforms
Security is an architecture, not a patch.
In modern distributed systems, security isn’t a feature you add after go-live—it’s the fabric of the system from the first whiteboard sketch to the last decommissioning script.
For large-scale, multi-cloud platforms, the secure SDLC is more than CI/CD scanners and a penetration test before launch. It’s a continuous, layered defense model where each layer of the infrastructure stack—code, container, compute, cluster, cloud, and edge—has its own controls, feedback loops, and threat-driven design patterns.
This post outlines a layer-by-layer security blueprint you can operationalize in real enterprise environments.
Product Planning & Architecture — Security from Whiteboard to PRD
Objective: Threat-model early, build controls into the system contract before a single commit exists.
| Security Requirement | Implementation Patterns | Key Risks if Ignored |
|---|---|---|
| Threat Modeling Docs, System Architecture, Product Overview | Map trust boundaries, attack surfaces, and high-value assets. Include abuse cases alongside user stories. | Blind spots in architecture, exploitable implicit trust |
| Code Scans Inventory of Git repos, folders, and modules | Run SAST/SCA on all repositories; ensure modules are mapped to owners; automate dependency checks in CI/CD. | Undetected vulnerable dependencies, unowned code paths |
| Cloud Security Review Cloud infra + container image inventory | Apply principle of least privilege, deny-by-default posture, authenticated inter-service calls only. Assess both existing and newly deployed components. | Service spoofing, lateral movement, exposure of unprotected assets |
| Pentesting Access to product environments & endpoints | Strong AuthN/AuthZ, schema validation, rate limiting, contract tests in CI. Scope includes both internal and external attack surfaces. | API abuse, injection attacks, privilege escalation |
| Data Classification | Tag data flows by confidentiality, integrity, and regulatory scope (GDPR, PCI DSS, HIPAA, FedRAMP). | Data exfiltration, regulatory fines |
1. Code — Shifting Security to the Commit
Objective: Block vulnerabilities before they reach artifact builds.
| Control | Practice | Tooling Examples |
|---|---|---|
| SAST | Run on every PR pre-merge, break builds for critical issues. | Semgrep, CodeQL, SonarQube |
| SCA | Identify vulnerable dependencies; auto-PR with safe versions. | Snyk, Dependabot |
| Secrets Scanning | Prevent commits of API keys, passwords, tokens. | Gitleaks, Trufflehog |
| Architectural Reviews | Security architects sign-off on sensitive code flows. | Internal review gates |
2. Container — Building Immutable, Hardened Artifacts
Objective: Ship minimal, verified, and locked-down runtime images.
| Control | Pattern | Why It Matters |
|---|---|---|
| Golden Base Images | Internal registry, CIS-hardened, signed (cosign/notary). | Eliminates untrusted base risk |
| SBOMs | Generated at build; stored in artifact repo. | Enables targeted vuln response |
| Non-Root Execution | Drop capabilities, run read-only FS, apply seccomp/AppArmor profiles. | Mitigates container breakout |
| Slim/Distroless | Only required binaries; small attack surface. | Reduces exploit vectors |
3. Compute — Securing Core Workloads
Objective: Strong identity, encryption, and runtime visibility.
| Control | Pattern | Cloud-Native Examples |
|---|---|---|
| AuthN/AuthZ | Service identities bound to roles, no shared creds. | AWS IAM Roles, GCP Service Accounts |
| Encryption | TLS 1.3 in transit, KMS/BYOK at rest. | AWS KMS, Azure Key Vault |
| OS Hardening | CIS baselines, auto-patching, drift detection. | Ansible, Chef InSpec |
| Runtime Threat Detection | eBPF-based syscall monitoring; anomaly alerts. | Falco, Tetragon |
4. Cluster — Kubernetes and Beyond
Objective: Isolate, observe, and enforce zero-trust at the orchestration layer.
| Control | Pattern | Notes |
|---|---|---|
| RBAC | Namespace-scoped roles; no cluster-admin defaults. | Prevents privilege escalation |
| Network Policies | Deny-by-default pod-to-pod comms. | Stops lateral movement |
| Service Mesh mTLS | End-to-end encryption & workload identity. | Istio, Linkerd |
| eBPF Sensors | Detect privilege escalation or network anomalies. | CNAPP agent integration |
5. Cloud — Multi-Cloud Governance & Detection
Objective: Detect misconfigurations, enforce policy, respond in near-real-time.
| Control | Pattern | Tools |
|---|---|---|
| CSPM | Continuous config scans, drift detection vs. golden baseline. | Prisma Cloud, Wiz |
| CWP | Protect runtime workloads against exploits. | Defender for Cloud, Aqua |
| SIEM/SOAR | Unified logging, automated playbooks for containment. | Splunk, Sentinel |
| Auto-Remediation | Policy violations trigger IaC fixes or service disablement. | Cloud Functions, Lambda hooks |
6. CDN & Edge — Securing the Delivery Perimeter
Objective: Minimize exposure at the global ingress points.
| Control | Pattern |
|---|---|
| TLS Everywhere | Enforce TLS 1.3, HSTS, modern ciphers. |
| WAF & Bot Mitigation | Protect against OWASP Top 10 + credential stuffing. |
| DDoS Protection | Layer 3–7 defense; scrubbing centers. |
| Isolated Edge Functions | Min privilege, no shared runtime context. |
Final Thoughts
A secure SDLC for distributed, multi-cloud systems is not about adding more scanners—it’s about designing an ecosystem where controls are inherent, automated, and self-correcting.
Every layer—from whiteboard to edge cache—needs explicit security guarantees, verified continuously.